In today's digital landscape, security is paramount for any organization, and Amazon Web Services (AWS) are no exception. With its vast array of features and services, AWS offers multiple layers of security to help safeguard your infrastructure and data. One such security measure is multi-factor authentication (MFA), which plays a critical role in strengthening the security of your AWS account.
What is MFA?
Multi-factor authentication (MFA) is a security measure that requires a user to provide two or more forms of authentication before gaining access to a system or application. This is in contrast to single-factor authentication, which only requires a single form of authentication such as a password or PIN.
Why do you need MFA?
By requiring multiple forms of authentication, MFA makes it more difficult for attackers to gain access to a user's accounts or sensitive information even if they manage to obtain one factor of authentication. This helps to improve the overall security of a system or application. Enabling MFA in your AWS account is a simple step that can greatly enhance the security of your infrastructure and help prevent unauthorized access to your sensitive data and resources. It is highly recommended to enable MFA on all of your AWS accounts, especially for accounts that have access to critical resources or hold sensitive data.
Risks associated if MFA is not enabled
Without Multi-Factor Authentication (MFA) enabled, there are several risks that can threaten the security of an AWS account which include:
- Password theft
Passwords can be stolen through phishing attacks, social engineering, or other means. If an attacker gains access to your password, they can use it to access your AWS account and potentially compromise your resources and data. - Brute-force attacks
Attackers can attempt to guess your password using automated tools, which can take advantage of weak or easily guessable passwords. Enabling MFA helps prevent brute-force attacks because the attacker would also need to provide a second authentication factor to access the account. - Compromised credentials
If a user's AWS access key or secret access key is compromised, an attacker can use those credentials to access your AWS resources. Enabling MFA helps prevent unauthorized access even if the credentials are compromised. - Unauthorized access to resources
Without MFA, an attacker could potentially access your AWS resources, modify or delete them, and cause damage to your infrastructure and business. - Compliance violations
Many regulatory frameworks require MFA for access to sensitive data or critical infrastructure. If you do not have MFA enabled, you may be in violation of compliance requirements, which can result in fines or legal action.
How to enable MFA
Enable MFA for the root account first. The root user can perform sensitive operations in your account, adding this additional layer of authentication helps you to better secure it.
To enable MFA for root account:
- Log in to your AWS Management Console using your root account credentials.
- Click on your username in the top right corner of the screen and select "My Security Credentials" from the dropdown menu.
- In the "MFA" section, click "Activate MFA".
- Select "A virtual MFA device" or "A U2F security key" as your MFA device type. A virtual MFA device generates codes on a smartphone app or a hardware token, while a U2F security key is a physical device that plugs into your computer's USB port.
- Follow the instructions to set up your MFA device. This will typically involve scanning a QR code with your smartphone app or inserting the U2F key into your computer and pressing a button.
- Once your MFA device is set up, you will need to enter the code generated by your MFA device in addition to your password whenever you log in to your root account.
Important: Enabling MFA on your root account does not automatically enable MFA for all IAM users in your account. You will need to individually enable MFA for each IAM user that requires access to your AWS resources. Additionally, you should ensure that you have backup MFA devices and processes are in place in case your primary MFA device is lost, stolen, or otherwise unavailable.
The IAM policies that enable MFA for AWS users are typically managed by the AWS account owner or an administrator with appropriate permissions. The account owner or administrator can create and manage IAM policies that grant permissions to users to enable MFA on their accounts. Please attach The IAM policy to the required IAM users via AWS Management Console, AWS CLI, or AWS SDKs so that the user can Manage their MFA devices and set MFA by themselves.
To enable MFA for IAM users:
- Log in to your AWS Management Console using your root account credentials.
- Navigate to the IAM console by clicking on "Services" in the top left corner, and selecting "IAM" under the "Security, Identity, & Compliance" section.
- In the left navigation pane, click on "Users" and then click on the IAM user for whom you want to enable MFA.
- In the "Security credentials" tab, click "Manage" next to "Assigned MFA device".
- Click "Virtual MFA device" or "U2F security key" to add a new MFA device.
- Follow the instructions to set up the new MFA device, which typically involves scanning a QR code with a smartphone app or inserting a U2F key into the computer and pressing a button.
- Once the MFA device is set up, you will see a new field in the "Assigned MFA device" section with the MFA device's serial number.
- Click "Activate MFA" to enable MFA for the IAM user.
- Provide the user's contact information in case they lose their device, and then click "Assign MFA".
Note: Once MFA is enabled for an IAM user, the user will need to provide their MFA device code in addition to their username and password to access your AWS resources.
What is MFA device enforcement?
MFA device enforcement refers to the process of setting up and enforcing the use of specific MFA devices for user authentication. When MFA device enforcement is enabled, users are required to use a particular MFA device, such as a hardware token, a software token on a mobile device, or a biometric factor, to authenticate their identity before accessing a system or service.
Why do we need MFA device enforcement?
MFA device enforcement can be an effective way to improve security for systems and services that require strong authentication, especially those that store sensitive data or handle financial transactions.
How to enable MFA device enforcement
- Open the IAM Identity Center console.
- In the left navigation pane, choose Settings.
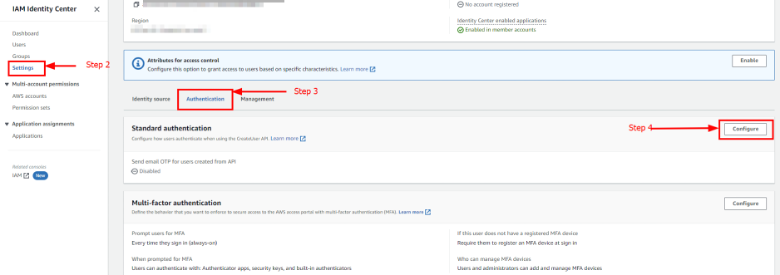
- On the Settings page, choose the Authentication tab.
- In the Multi-factor authentication section, choose Configure.
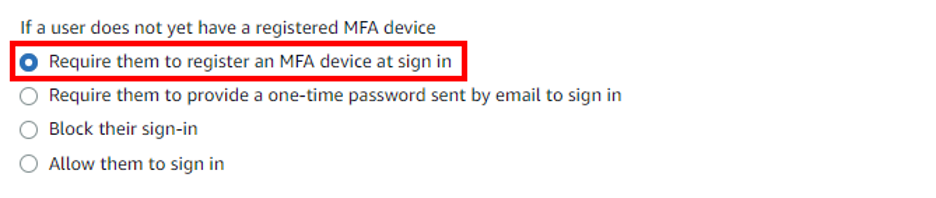
- On the Configure multi-factor authentication page, under “If a user does not yet have a registered MFA device” choose “Require them to register an MFA device at sign in”
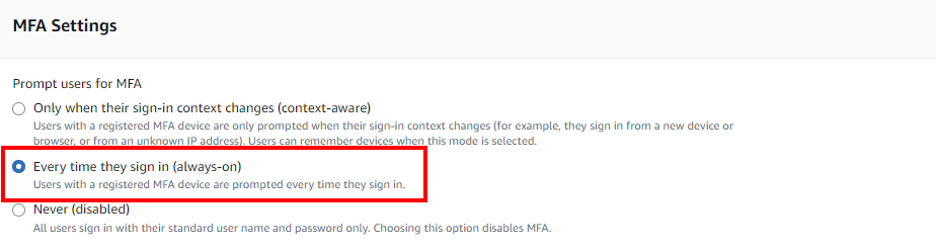
- On the Configure multi-factor authentication page, under “Prompt users for MFA” choose “Every time they sign in (always-on)”
Conclusion
Enabling MFA is a crucial step in enhancing the security of your AWS account. By requiring multiple forms of authentication, MFA significantly reduces the risk of unauthorized access to your infrastructure and sensitive data. It is highly recommended to enable MFA on all of your AWS accounts. With proper permissions, Gradient Cyber can help you enable MFA for your IAM users. Gradient Cyber monitors your IAM logs for MFA logins and updates you if this setting is not enabled.
Learn more about how managed cloud detection and response (CDR) can protect your organization's cloud workloads and applications. Or, if your detection and response needs are more extensive, check out our comprehensive MXDR solution to see how Gradient Cyber MXDR can help protect all on-premises and cloud environments from cyber attacks.


.png?height=500&name=GC%20+%20IM%20Logo%20(38).png)

.png?height=500&name=GC%20+%20IM%20Logo%20(37).png)